Understanding the Significance of BPDU Guard in Network Security
The dynamic BPDU Guard protocol, which is used in computer networking, is essential for boosting network security and dependability. While BPDU Guard’s main objectives are to protect network integrity and stop unwanted changes, it works in concert with Spanning Tree Protocol (STP) to accomplish these goals. The importance of BPDU Guard, its features, and its critical role in upholding a secure and reliable network infrastructure will all be covered in this article.
The Role of BPDU Guard
As mentioned earlier, Spanning Tree Protocol is crucial for maintaining a stable network by eliminating loops and providing redundancy. However, its primary focus is on topology and path selection, not on security. STP alone does not address issues related to unauthorized switches, misconfigured devices, or rogue elements that can potentially disrupt network operations.
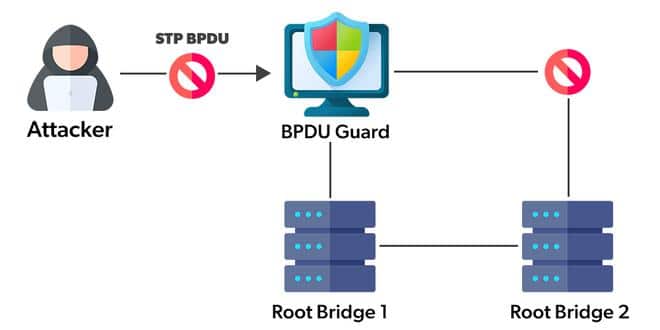
This is when the supplementary functionality of BPDU Guard comes into play. BPDU Guard keeps an eye out for the Bridge Protocol Data Units (BPDUs), which are necessary for STP to function, on switch ports. Switches, their priorities, and the network’s structure are all described in BPDUs. BPDUs shouldn’t be present on ports connected to end-user devices or unauthorized switches in a conventional network; they should only pass between authorized network switches.
Preventing Unauthorized Switches
Preventing illegal switches from being connected to the network is one of BPDU Guard’s main duties. Only genuine network switches should be connected to switch ports in a properly configured network. It is possible, nonetheless, for unauthorized switches or improperly configured devices to be connected into network ports.
The ports that BPDU Guard is configured on are watched over by it like a sentinel. It immediately disables the port when it discovers BPDUs on a port that shouldn’t be receiving them (such a port associated with an end device or an unlawful switch). The risk posed by unauthorized or malicious devices is effectively reduced by this quick response, which also successfully inhibits the formation of network loops.
Security Enhancement
By swiftly separating possibly hacked or rogue devices, BPDU Guard improves network security in addition to loop prevention. When a device attached to a switch port begins to produce BPDUs, it can be an unauthorised device trying to interfere with the network. The rapid response of BPDU Guard makes sure that such devices are quickly unplugged from the network, lowering the chance of security breaches.
Monitoring and Alerting
When BPDU Guard disables a port, it can produce alerts or log entries; this functionality is crucial for network monitoring and troubleshooting as it allows administrators to look into the cause of the port shutdown, identify potential security threats, and take appropriate action to resolve the issue.
Implementing BPDU Guard
Network administrators must enable and configure BPDU Guard on their network switches in order to take advantage of its features. An overview of the essential steps is provided below:
1. Enable BPDU Guard:
First and foremost, administrators need to enable BPDU Guard on the switches that support this feature. Most modern managed switches offer BPDU Guard as part of their feature set.
2. Apply BPDU Guard Selectively:
Administrators have the option to selectively install BPDU Guard to particular switch ports. It is typically used on ports that are solely anticipated to be used by end users or as uplinks to other switches.
3. Monitoring and Alerting:
Once activated, the BPDU Guard continuously checks the defined ports for BPDUs. It performs specified actions, like as blocking the port or sending out alarms, when it discovers an unlawful BPDU.
4. Port Recovery (Optional):
After BPDU Guard disables a port, administrators could in some circumstances want to activate automatic port recovery. This can be set up to enable the port automatically after a predetermined amount of time or following user intervention.
5. Log and Audit:
It’s crucial to often analyze the audit reports and logs produced by BPDU Guard. This aids in the quick identification and mitigation of any anomalies or security issues.
Conclusion
Network administrators rely on BPDU Guard as a vital tool in their toolbox to assist them successfully negotiate the challenges of contemporary networking in an era where network dependability and security are of utmost importance.