Operating System – Access metrics mechanism Long Questions Answers
 Here in this section of Operating System Long Questions and Answers,We have listed out some of the important Long Questions with Answers on Access metrics mechanism. which will help students to answer it correctly in their University Written Exam.
Here in this section of Operating System Long Questions and Answers,We have listed out some of the important Long Questions with Answers on Access metrics mechanism. which will help students to answer it correctly in their University Written Exam.Lists of Long Descriptive type Questions that may be asked in Written Exams.
- (1) Explain Access metrics mechanism.
Question -1 Explain Access metrics mechanism.
Model of protection can be viewed abstractly as a matrix called an access matrix.
- Row of access matrix represents domains and a column represents objects.
- Each entry in the matrix consists of set of access rights.
- The entry access (i, j) defines set of operations that a process executing in domain Di, can invite an object Oj.
- The access matrix scheme provides us with the mechanism for specifying a variety of policies.
- We must ensure that process executing in domain D can access only those objects specified in row P as allows by the access matrix.
- Access matrix also provides the mechanism of defining and implementing control for both static and dynamic association between process and domains.
- We are executing an operation on an object.
- We can control these changes by including the access matrix as an object.
- Operations on domains and the access matrix are not in themselves important.
- Important is that they illustrate the ability of the access matrix model to allow the implementation and control of dynamic protection requirements.
- New objects and new domains can be created dynamically and included in access matrix model.
- We need to consider only the operations that are possible on these new objects (domains and access matrix) and decide how we want processes to be able to execute these operations.
- Allowing controlled change to the contents of the access matrix entries requires three additional operations: copy, owner and control.
- The ability to copy an access right from one domain (row) of the access matrix to another is denoted by asterisk (*) appended to the access right.
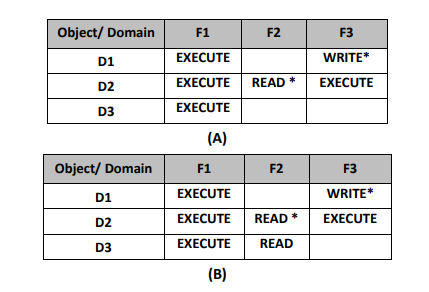
- For example as shown in figure (A) a process executing in domain D2 can copy the read operation into any entry associated with file F2.
- Hence the access matrix of figure (A) can be modified into figure (B).
- We also need mechanism to allow addition of owner rights and removal of some rights.
- The ownership right controls these operations.
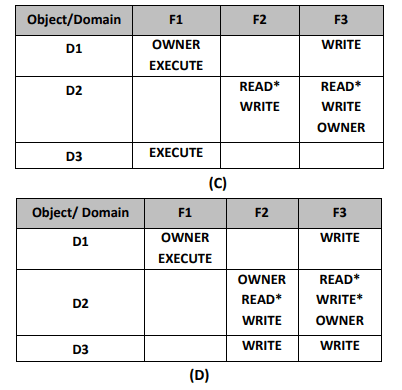
- For example figure (C) domain D1 is the owner of F1 and thus can add and delete any valid right in column F1.
- Similarly Domain D2 is the owner of F2 and F3 and thus can add and remove any valid right within these two columns.
- Thus the access matrix figure (C) can be modified to the access matrix shown in figure (D).
- The copy and owner rights allow a process to change the entries in a column. A mechanism is needed to change the entries in row.
- If access (i, j) includes the control right then a process executing in domain Di can remove any access right from row j.
- These operations on the domains and the access matrix are not in themselves particularly model to allow implementation and control of dynamic protection requirements.