Operating System – Access Control list Long Questions Answers
 Here in this section of Operating System Long Questions and Answers,We have listed out some of the important Long Questions with Answers on Access Control list which will help students to answer it correctly in their University Written Exam.
Here in this section of Operating System Long Questions and Answers,We have listed out some of the important Long Questions with Answers on Access Control list which will help students to answer it correctly in their University Written Exam.Lists of Long Descriptive type Questions that may be asked in Written Exams.
- (1) What is Access Control list? Explain in brief..
Question-1 What is Access Control list? Explain in brief.
- Most of domains have no access at all to most objects, so storing a very large, mostly empty, Access matrix is a waste of disk space.
- Two methods are practical; the first is storing the matrix by rows and the second method is storing the matrix by columns, and then storing only the nonempty elements.
- The two approaches are surprisingly different.
- The first technique consists of associating with each object an (ordered) list containing all the domains that may access the object, and how.
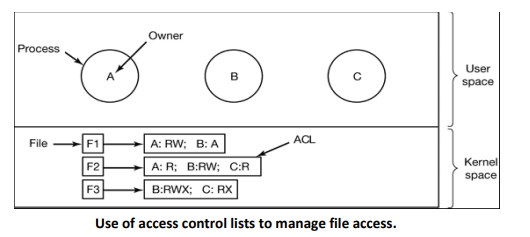
- This list is called the Access Control List or ACL and is illustrated in Figbelow.
- Here we see three processes A, b, and C, each belonging to a different domain. There are three files F1, F2, and F3.
- For simplicity, we will assume that each domain corresponds to exactly one user, in this case, users are A, B, and C.
- Often in the security literature, the users are called subjects or principals, to contrast them with the things owned, the objects, such us files.
- Each file has an ACL associated with it. File F1 has two entries in its ACL (separated by a semicolon).
- The first entry says that any process owned by user A may read and write the file. The second entry says that any process owned by user B may read the file.
- All other accesses by these users and all accesses by other users are forbidden.
- Note that the rights are granted by user, not by process.
- As far as the protection system goes, any process owned by user A can read and write file F1. It does not matter if there is one such process or 100 of them. It is the owner,not the process ID that matters.
- File F2 has three entries in its ACL: A, B, and C can all read the file, and in addition B can also write it.
- No other accesses are allowed, File F3 is apparently an executable program, since B and C can both read and execute it. B can also write it.
- Many systems support the concept of a group of users. Groups have names and can be included in ACLs.
- The other way of slicing up the matrix of Fig above is by rows.
- When this method is used, associated with each process is a list of objects that may be accessed, along with an indication of which operations are permitted on each, in other words, its domain.
- This list is called a capability list or C-list and the individual items on it are called capabilities.